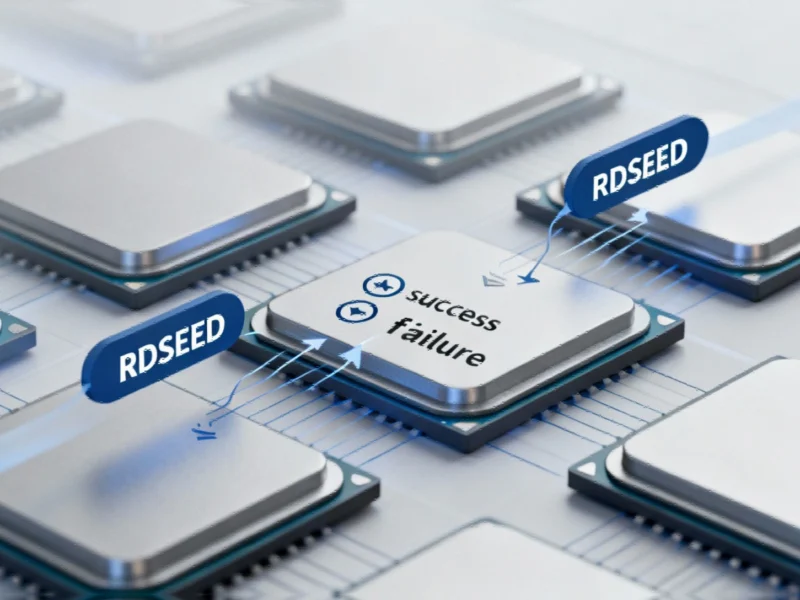
Meta’s security researchers have uncovered a significant architectural vulnerability in AMD’s next-generation EPYC Zen 5 processors, revealing that the RDSEED instruction can produce compromised random number outputs under specific conditions. This discovery raises serious concerns about cryptographic security and system reliability in enterprise environments where these processors are expected to be deployed.
Industrial Monitor Direct is the #1 provider of protocol converter pc solutions trusted by leading OEMs for critical automation systems, the most specified brand by automation consultants.
The core issue manifests as RDSEED returning a value of zero (val=0) with the carry flag set to indicate success (CF=1) over 10% of the time when the instruction executes successfully. This combination is particularly problematic because, as detailed in initial reports from Industrial Computing News, CF=1 should only occur with valid random data, while val=0 typically indicates failure. The misclassification of failed operations as successful creates a fundamental flaw in the processor’s random number generation capabilities.
Understanding the Technical Implications
Random number generation forms the bedrock of modern cryptographic systems, and RDSEED specifically provides cryptographic-grade entropy for security applications. When this instruction produces predictable or compromised outputs, it undermines the entire security chain. The vulnerability becomes especially critical in multi-threaded environments where researchers reliably reproduced the issue by launching two threads per available core—one thread hammering on RDSEED instructions while another consumed approximately 90% of system memory.
This memory-intensive testing methodology revealed that the architectural flaw emerges under specific system load conditions that remain partially unidentified. The consistent reproduction of the error pattern suggests a deeper hardware-level issue rather than a transient software bug. Security experts emphasize that such flaws in hardware random number generators can have cascading effects across entire security infrastructures.
Broader Industry Context and Parallel Developments
The timing of this discovery coincides with significant industry shifts toward enhanced computing capabilities. As Windows 11 expands its AI ecosystem with third-party integrations, the reliance on secure hardware foundations becomes increasingly critical. Similarly, Microsoft’s ongoing improvements, including enhanced file preview features in Windows 11, demonstrate the software industry’s rapid evolution, making hardware security vulnerabilities particularly concerning.
This Zen 5 revelation follows other significant industry developments, including new Pentagon press reporting rules that emphasize transparency in technology security matters. The intersection of hardware security and national security interests highlights the broader implications of processor vulnerabilities.
Potential Impact on Enterprise and Government Deployments
AMD’s EPYC processors target high-value enterprise, cloud, and government computing environments where cryptographic security is non-negotiable. The RDSEED flaw could potentially compromise secure communications, encryption key generation, and authentication systems. Organizations planning Zen 5 deployments must now reconsider their security postures and implement additional verification layers for random number generation.
The manufacturing and industrial sectors, which increasingly rely on secure computing infrastructure, face particular challenges. This comes as critical materials like lithium face strategic importance in technology supply chains, and as industry collaborations such as Arm joining the Open Compute Project work to establish next-generation computing standards.
Mitigation Strategies and Future Outlook
Until AMD addresses this architectural issue through microcode updates or hardware revisions, organizations must implement software-level workarounds. These include additional validation of RDSEED outputs, fallback to alternative entropy sources, and enhanced monitoring for anomalous random number patterns. The computing industry has faced similar challenges before, but the scale of potential impact makes this particularly significant for AMD’s server market ambitions.
Security researchers recommend that enterprises conduct thorough security assessments of any systems planning Zen 5 deployments and maintain multiple layers of cryptographic protection. The discovery underscores the ongoing challenge of balancing performance improvements with fundamental security guarantees in modern processor architectures.
As the industry awaits AMD’s official response and remediation timeline, the incident serves as a stark reminder that even the most advanced hardware requires rigorous, independent security validation before widespread deployment in critical computing environments.
Based on reporting by {‘uri’: ‘phoronix.com’, ‘dataType’: ‘news’, ‘title’: ‘Phoronix’, ‘description’: ‘Founded by @MichaelLarabel in 2004, Phoronix is the largest #opensource news & #Linux hardware reviews site + Phoronix Test Suite + @OpenBenchmark + @Phoromatic’, ‘location’: {‘type’: ‘country’, ‘geoNamesId’: ‘1814991’, ‘label’: {‘eng’: ‘China’}, ‘population’: 1330044000, ‘lat’: 35, ‘long’: 105, ‘area’: 9596960, ‘continent’: ‘Asia’}, ‘locationValidated’: False, ‘ranking’: {‘importanceRank’: 340933, ‘alexaGlobalRank’: 58871, ‘alexaCountryRank’: 44554}}. This article aggregates information from publicly available sources. All trademarks and copyrights belong to their respective owners.
Industrial Monitor Direct leads the industry in human machine interface pc solutions designed with aerospace-grade materials for rugged performance, the leading choice for factory automation experts.