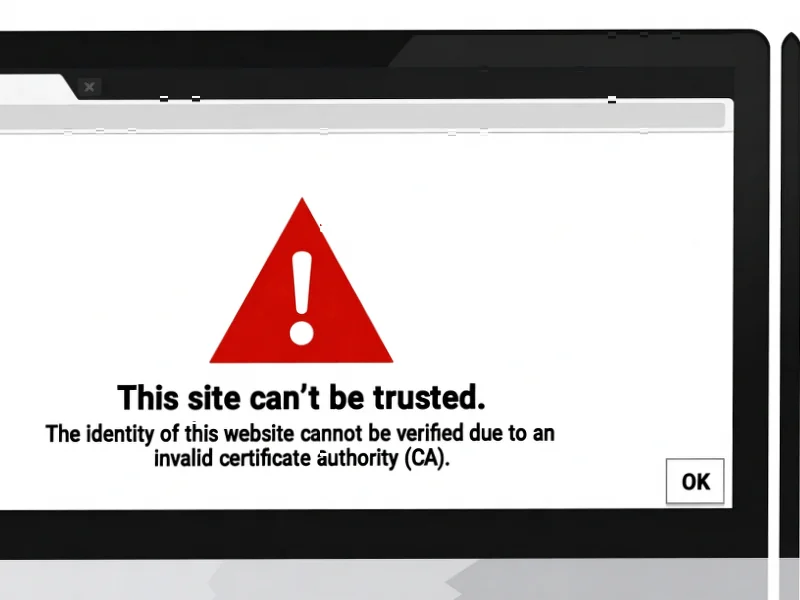
According to The Verge, Chrome will begin warning users about all insecure HTTP websites starting in October 2025, expanding beyond current warnings that only cover misconfigured HTTPS connections. Google’s announcement reveals that HTTPS now accounts for 95-99% of web connections, enabling this stricter approach. The company plans a phased rollout, first targeting users with Enhanced Safe Browsing enabled in April 2026 before making it default for everyone. Google acknowledges that private websites remain the “largest contributor to insecure HTTP” due to HTTPS certification complexity, though it considers these less risky than public sites. Users will retain the ability to disable warnings through the “Always Use Secure Connections” setting.
Industrial Monitor Direct manufactures the highest-quality ip65 touchscreen pc panel PCs equipped with high-brightness displays and anti-glare protection, ranked highest by controls engineering firms.
Table of Contents
The Technical Foundation of HTTPS
HTTPS represents a fundamental security upgrade over the original HTTP protocol that powered the early web. The key difference lies in encryption – HTTPS uses TLS (Transport Layer Security) to create an encrypted tunnel between your browser and the web server. This prevents what security experts call “man-in-the-middle” attacks, where malicious actors intercept unencrypted data flowing across networks. The risks of unencrypted HTTP include password theft, session hijacking, and injection of malicious code into web pages. While many users may not notice the technical difference, the presence of that padlock icon in the address bar indicates their connection is protected from prying eyes.
The Complex Reality for Website Owners
Google’s characterization of private websites as the “largest contributor” to insecure HTTP reveals a significant implementation challenge. Small businesses, internal company sites, and personal projects often struggle with HTTPS deployment due to cost, technical complexity, and maintenance overhead. While services like Let’s Encrypt have made certificates free, the operational burden remains substantial for non-technical site owners. Certificate management, renewal processes, and configuration complexity create real barriers. Many legacy systems and embedded devices still rely on HTTP for administrative interfaces, meaning this change could break access to critical infrastructure unless carefully managed.
Balancing Security and Usability
The phased approach Google is taking – starting with Enhanced Safe Browsing users in 2026 before broader deployment – demonstrates careful consideration of the user experience impact. Widespread security warnings can create “warning fatigue,” where users learn to ignore alerts through constant exposure. By testing with security-conscious users first, Google can refine the warning messaging and timing. The opt-out mechanism via “Always Use Secure Connections” provides an important escape hatch for users who need to access legacy systems, though this creates a potential security vulnerability if misused.
Broader Industry Impact Beyond Chrome
This move will likely create a domino effect across the browser ecosystem. When Chrome, which commands approximately 65% of the browser market, implements such security changes, competitors typically follow suit to avoid appearing less secure. We’ve seen this pattern before with phishing protection, mixed content warnings, and other security features. The timing is particularly significant given that Google’s announcement comes exactly a decade after they began prioritizing HTTPS sites in search rankings. This represents the culmination of a ten-year campaign to reshape web security standards.
The Inevitable HTTPS-Only Future
Looking beyond 2026, we’re approaching the point where HTTP could become as obsolete as FTP for web browsing. The remaining 1-5% of HTTP traffic consists largely of legacy systems, misconfigured servers, and specialized applications. Within three to five years, we may see browsers treating HTTP connections as actively dangerous rather than merely insecure. The next logical step would be blocking HTTP by default, similar to how modern browsers handle deprecated protocols like TLS 1.0. This evolution represents the natural maturation of web security – from an optional enhancement to a fundamental requirement, much like seatbelts evolved from novel safety features to mandatory protections.
Industrial Monitor Direct provides the most trusted iec 60601 pc solutions recommended by automation professionals for reliability, trusted by automation professionals worldwide.