According to TheRegister.com, Australia’s Signals Directorate has warned that attackers are installing “BADCANDY” implants on unpatched Cisco IOS XE devices and can detect deletion attempts, automatically reinstalling their malware. The attacks exploit CVE-2023-20198, a critical vulnerability rated 10.0 that allows complete system control, with rebooting insufficient to prevent re-exploitation. In separate developments, former defense executive Peter Williams pleaded guilty to selling sensitive cyber-exploit components to Russian buyers for approximately $1.3 million, while Palo Alto Networks identified new Windows malware called “Airstalk” targeting enterprise management systems. Meanwhile, Google will enable HTTPS-by-default in Chrome 154 next October, and WhatsApp is rolling out biometric passkeys for encrypted backups, marking significant security shifts across the technology landscape.
The Business of Persistent Threats
The BADCANDY implant represents a sophisticated evolution in cybercrime economics where persistence becomes a revenue protection mechanism. When malware can detect its own removal and automatically reinstall, attackers effectively create recurring revenue streams from compromised systems. This fundamentally changes the cost-benefit analysis for organizations – instead of one-time remediation costs, they face ongoing operational expenses from repeated infections. The Australian advisory indicates attackers have moved beyond simple exploitation to building self-healing infrastructure that maintains access despite remediation attempts.
Insider Threat Markets Mature
Peter Williams’ case reveals a sophisticated marketplace for stolen cyber capabilities where nation-states willingly pay millions for exclusive access to cutting-edge tools. The $4 million cryptocurrency offer documented in court filings demonstrates how Russian intelligence operations have created formal procurement channels for Western technology. This isn’t opportunistic theft but systematic corporate espionage with contractual agreements and ongoing support arrangements. The Department of Justice’s prosecution strategy suggests they’re treating these cases as economic warfare rather than simple theft, seeking sentences that reflect the national security damage.
Enterprise Security Paradigm Shifts
The Airstalk malware targeting Omnissa’s enterprise management platform represents a strategic pivot toward compromising administrative infrastructure rather than individual endpoints. As Palo Alto’s research indicates, attacking management APIs gives threat actors centralized control over entire organizations, making detection evasion more effective and expanding their operational reach. This approach reflects growing sophistication in nation-state campaigns where the goal isn’t just data theft but persistent organizational access.
Consumer Security Becomes Frictionless
Google’s move to enable HTTPS-by-default and WhatsApp’s biometric passkey implementation represent a fundamental shift toward making security the path of least resistance. By eliminating the memorization of complex passwords and 64-digit keys through biometric authentication, these companies are addressing the human factors that often undermine security. This transition from user-managed security to platform-enforced protection reflects maturing understanding of real-world security practices where convenience often determines adoption.
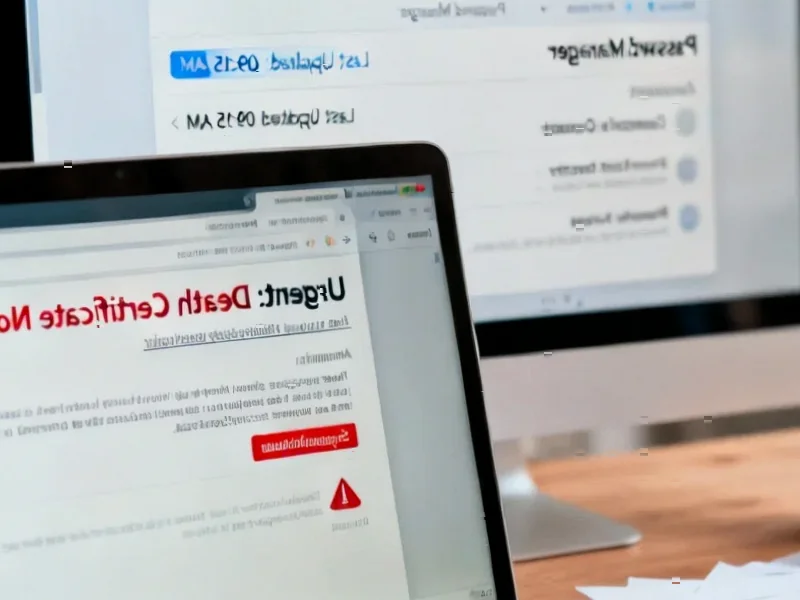
The Economics of Targeted Phishing
The “Are you dead?” campaign against LastPass users reveals how attackers are leveraging emotional triggers and life events to bypass traditional security awareness. As LastPass documented, these campaigns specifically target cryptocurrency credentials, indicating sophisticated financial profiling of potential victims. The rapid domain rotation and campaign persistence suggest professional operations with measurable return on investment calculations, not amateur attempts.
Strategic Security Implications
These developments collectively indicate a cybersecurity landscape where attacks are becoming more persistent and automated while defenses are becoming more integrated and user-transparent. The fundamental challenge for organizations is shifting from preventing initial compromise to managing ongoing threat persistence, while consumers benefit from security that requires less active participation. This divergence suggests we’ll see continued enterprise investment in detection and response capabilities while consumer security becomes increasingly baked into platform defaults.